Track threat actors and their techniques: Osint can uncover chatter on the dark web, hacker forums, or social media that hints at attacks, data breaches, or exploit techniques;. Gathering information on threat actors, tactics, and techniques. Utilizing osint to quickly assess and respond to security incidents. Some apps automatically give away information about youincluding your contacts, files stored on your device, and your geolocation datato third parties.
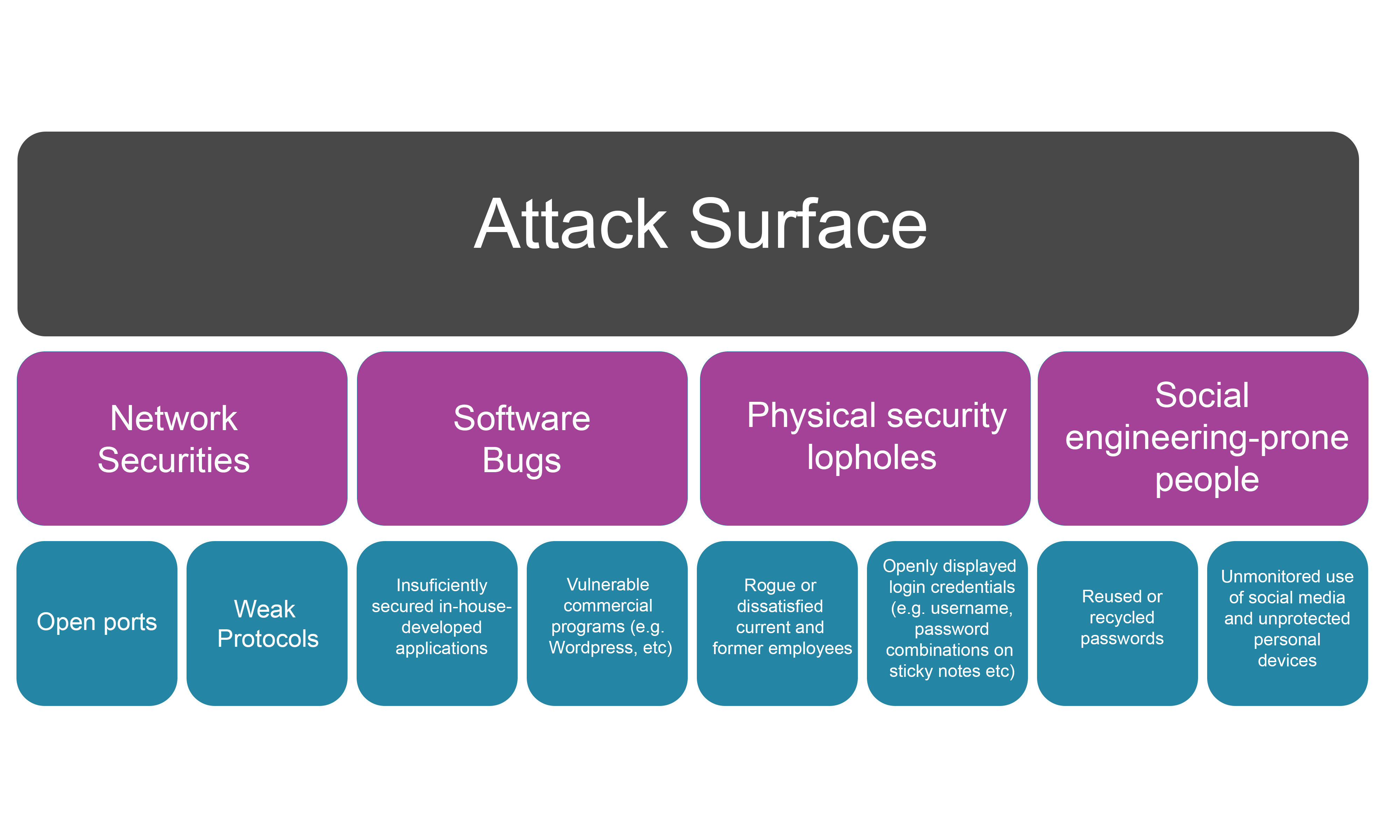
Identify publicly accessible data sources where sensitive information related to your business may be exposed, such as publicly accessible cloud storage, github repositories, or unprotected. Cybersecurity teams now rely on these tools to uncover hidden threats, map attack surfaces, and validate digital identities. This guide explores the top osint tools, sources, and. In cybersecurity, searching sites specialising in data breaches, such as have i been pwned, can help identify compromised credentials or exposed passwords.
Jenna Ortega's Style: Accident Or Intentional?
Charleygrayyy Leaked: The Shocking Truth Revealed
The Ebanie Bridges Leak: Truth Revealed